OSINT on the Ocean: Maritime Intelligence Gathering Techniques

As a rampant consumer of all things OSINT, learning more about Maritime OSINT has been on my to-do list for quite a while now. In an effort to expand my skills (and most importantly get better at Quiztime), I decided there is no better time than now to begin. Here I will break down several helpful sites for this kind of investigation work and then finish off with a quick case study example of how this information might be used.
The information that we might be looking for when doing this type of OSINT could be photos, travel logs, and crew information, or we could also come across Satcom transmissions. These days, all the various ships and vessels traveling in the ocean require geolocation to track their voyage to their ultimate destination; this means that each one is constantly transmitting data that can be picked up by people like me along the way. Fortunately for us, it is relatively easy to find this type of OSINT with a few simple-to-use websites.
Marinetraffic.com
Marinetraffic.com is one of the best known Maritime sites used for identifying tracking ships. The site is free to use unless you require satellite information on the ship’s current location and then it falls behind a paywall. Don’t worry, there is still a load of information we can gather on the free site.
The image you see below shows all of the current vessels in the ocean at the time of this screenshot, including cargo ships, tankers, passenger ships, high-speed boats, tug-boats, fishing boats, and yachts. On the left, the site allows you to filter based on type, capacity, year built, and length, as well as whether they are currently anchored.
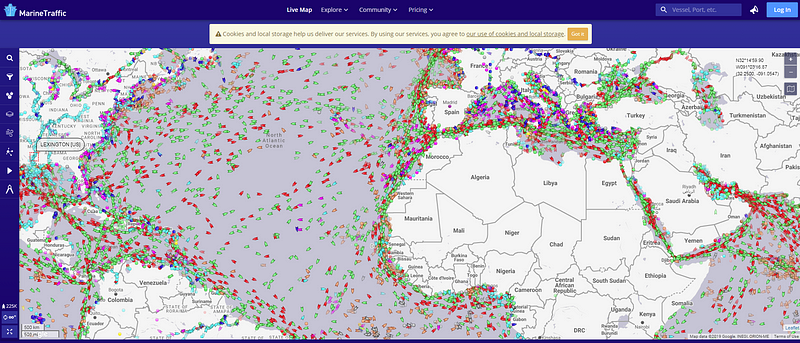
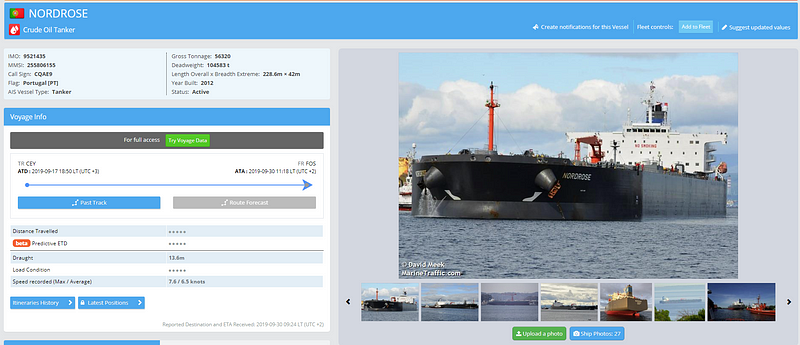
Unfortunately, without paying for the site, we are unable to select a specific ship on the above map. However, If you were to know the name of the ship you are looking for, you can search and bring up a lot of interesting details. For instance, while working on a recent Quiztime I knew the ship name was Nordrose so I dropped it into the search bar. This brings up a photo of the ship along with specific details like the call sign, weight, type, flag, and last position noted by satellite.
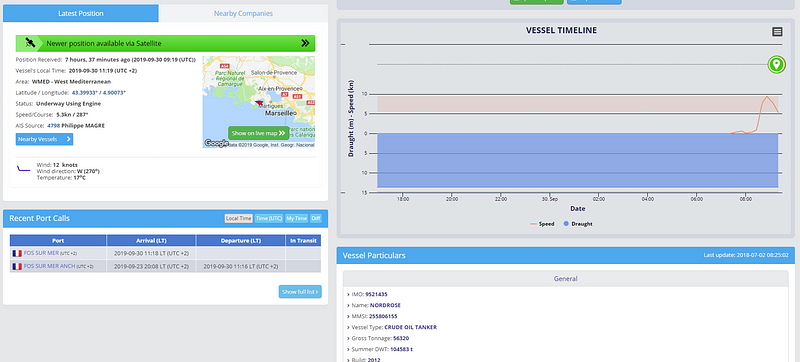
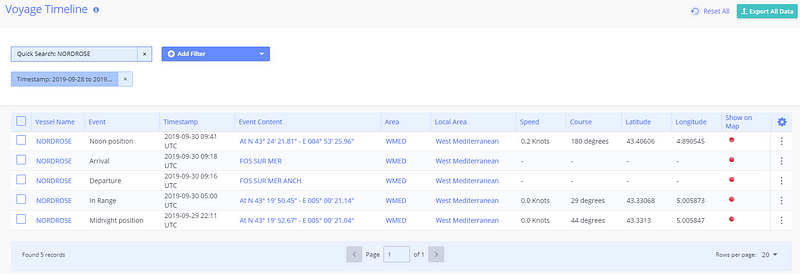
Also included on the site is a Voyage Timeline which displays the trip this specific ship has taken up to now. This would be particularly useful to verify that you have the correct ship based on previous sightings.
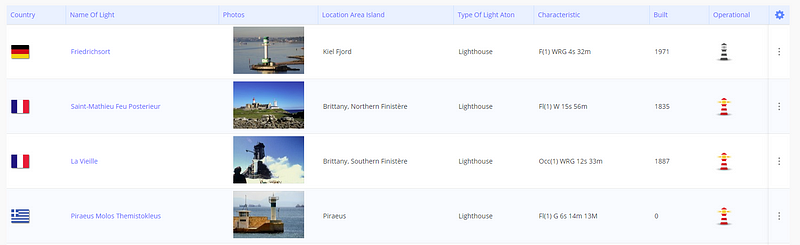
Additionally, this site also allows you to search for lighthouses based on area. If you ever need to locate a lighthouse, you can do it here.
Maritime-connector.com
This website differs from the first in that its main purpose is to facilitate a connection between ship workers and ship jobs. This comes in very handy for OSINT because it allows you to see an amazing amount of details about the crew.
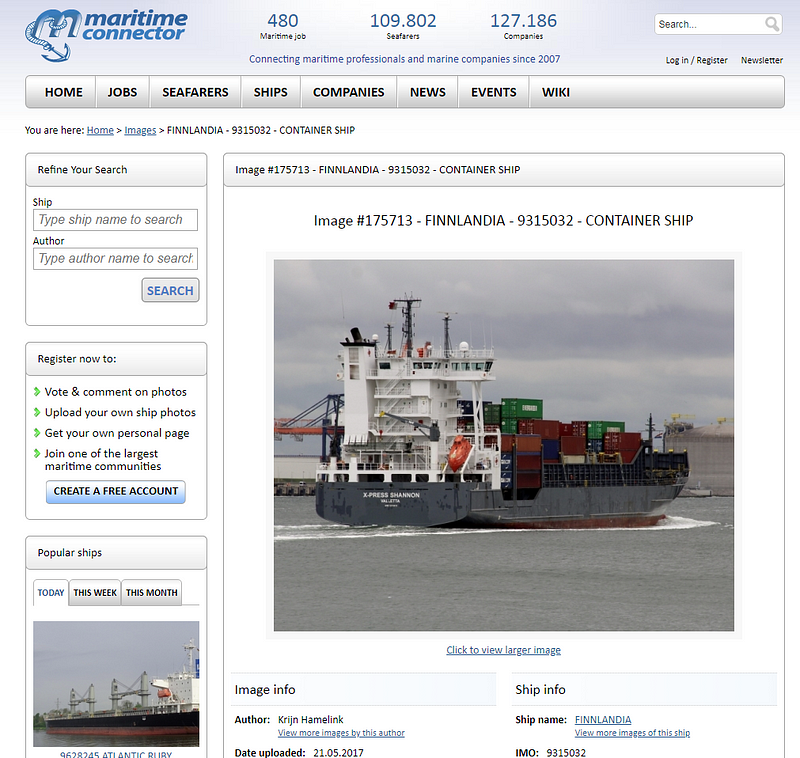
Once a ship is chosen, you can scroll down to the bottom and select to see open jobs on the ship as well as current employees. If you go to the Seafarers page, you will see a list of ship workers employed or seeking jobs. Think of it as a nautical LinkedIn.

Clicking on the first person on the list gives us a lot to work with even without having a subscription. In his listing, we are able to see that he is a Chief Officer who is married and from Croatia. We can also see his previous employment and current certifications.
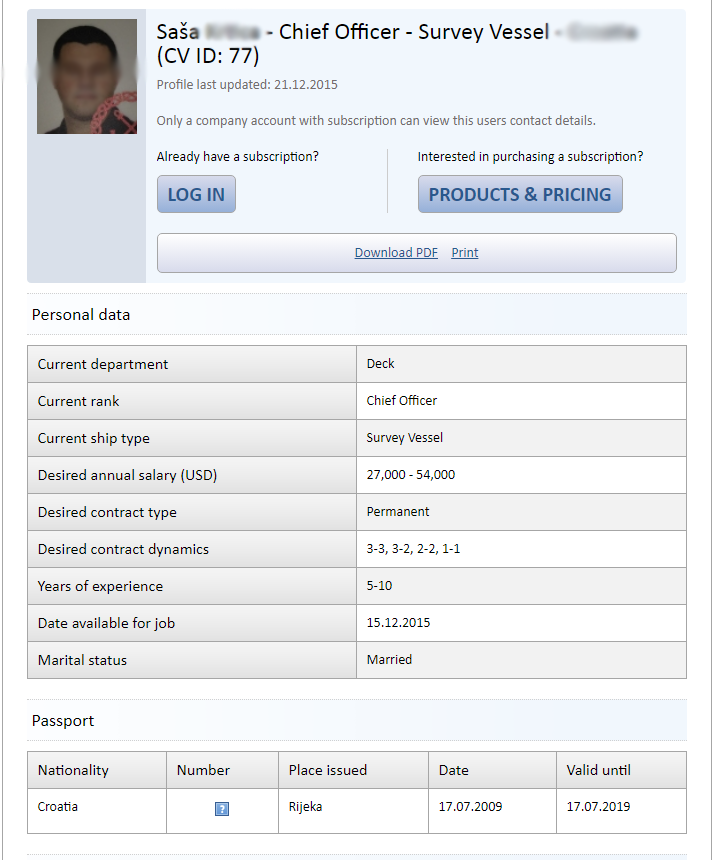
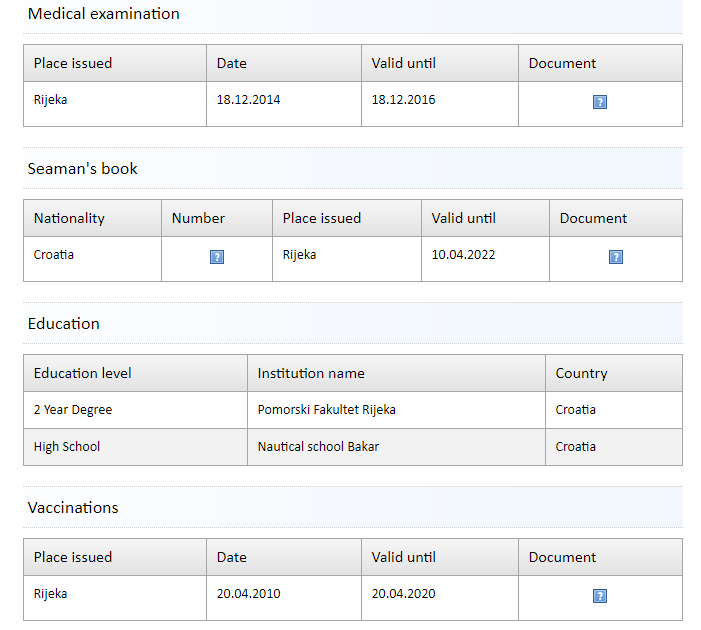
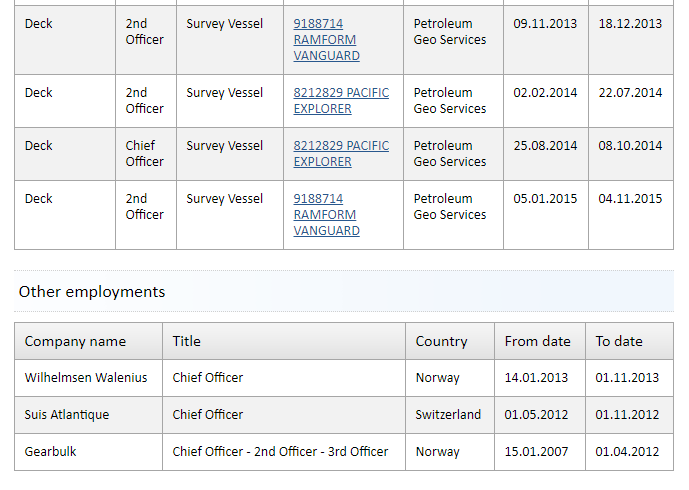
Without an account, we are unable to get access to his contact information but I will demonstrate in my case study exactly how easy that could be via LinkedIn.
Vesselfinder.com
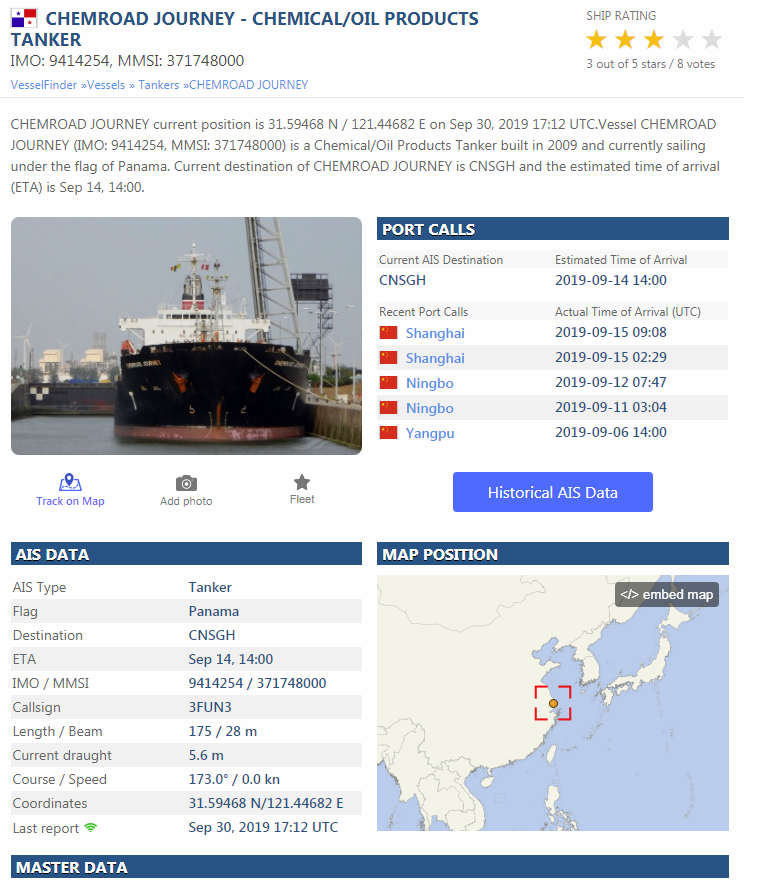
This site is very similar to marinetraffic.com in that it allows you to search for specific vessels on the ocean along with their details.
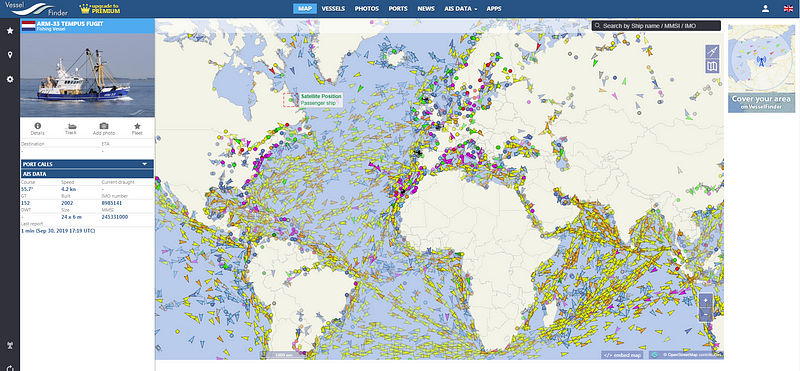
The one key difference I noted between the two sites is that Vesselfinder seems to provide more up-to-date AIS data without having a subscription.
Shodan
Shodan is another impressive tool that we can use for ship tracking purposes but in a slightly different capacity. I would like to note here that if you register Shodan with an .edu address you will get a free upgraded educational version with more options than you get on the free site.
Shodan works much like any other search engine, however, instead of searching websites, it searches for all the things connected to the internet. These things include webcams, smart appliances, wind turbines, and of course..ship communication systems. These items send a call out to the internet telling everyone what it is and what it does. Shodan listens for these calls, picks them up, and then displays the information provided.
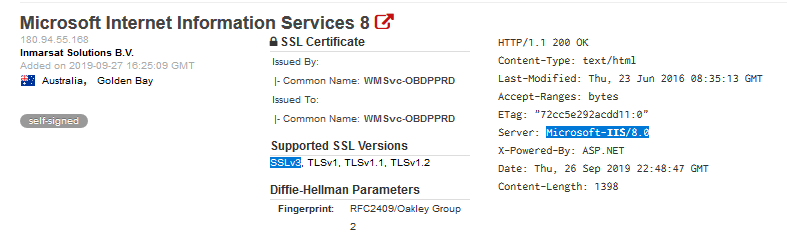
In this example below, I ran a search for Org: Inmarsat. Inmarsat is a top global mobile satellite communication system used in ships and would be present on many vessels in the ocean.
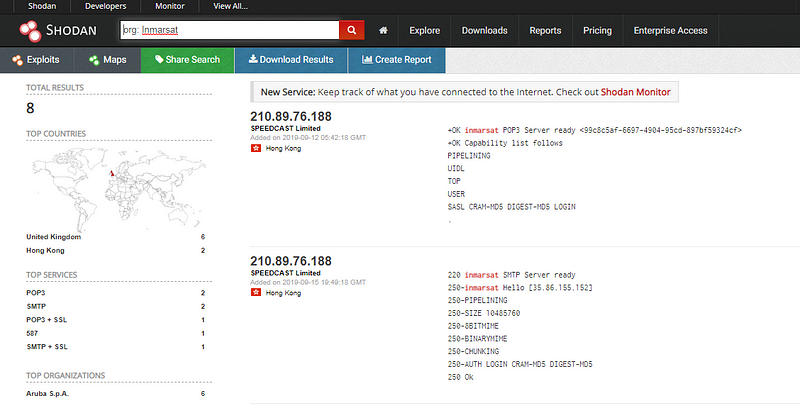
Depending on the specific criteria we add to the search we can get further details about the specific system, including what vulnerabilities may exist. Below we can see an SSL3 being used which can potentially allow an attacker to capture private data passed back and forth such as passwords that can then be used to gain deeper access.
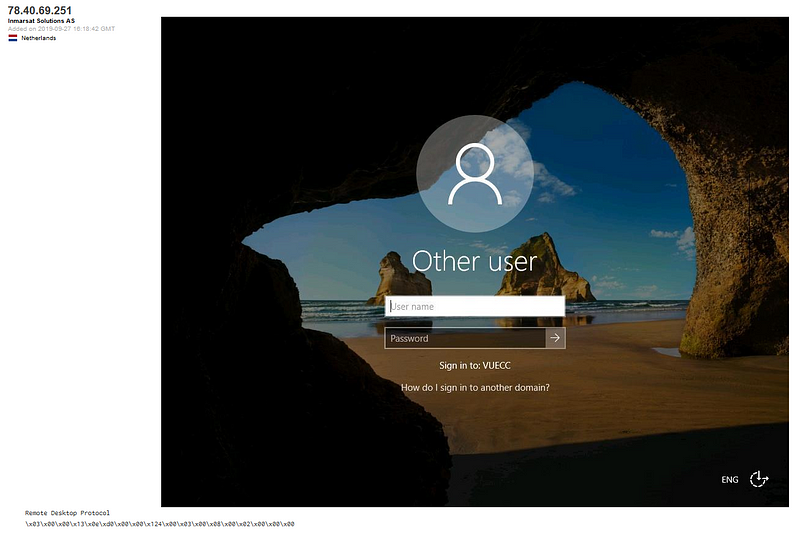
In another quick search of Shodan, this time focusing on port 3389 which is used for the remote desktop protocol we can see the login image of the server. From there we see the domain listed as VEUCC and the image says “Sign in to: VEUCC.” I would be concerned that this system may be vulnerable to certain Remote Desktop Protocol security vulnerabilities. I don’t want to go too far down the rabbit hole here but there are plenty of great writeups illustrating how these vulnerabilities can be exploited.
But what is VEUCC? We will find out below in my quick case study!
A Quick Case Study Using VUECC Example:
Now that we have learned about some of the ways to gather information, let’s piece them together into an investigation. Using the info we pulled in from Shodan, I did a quick Google search for “VUECC Netherlands.” It appears to be a sea transportation company located in Europe called UECC.
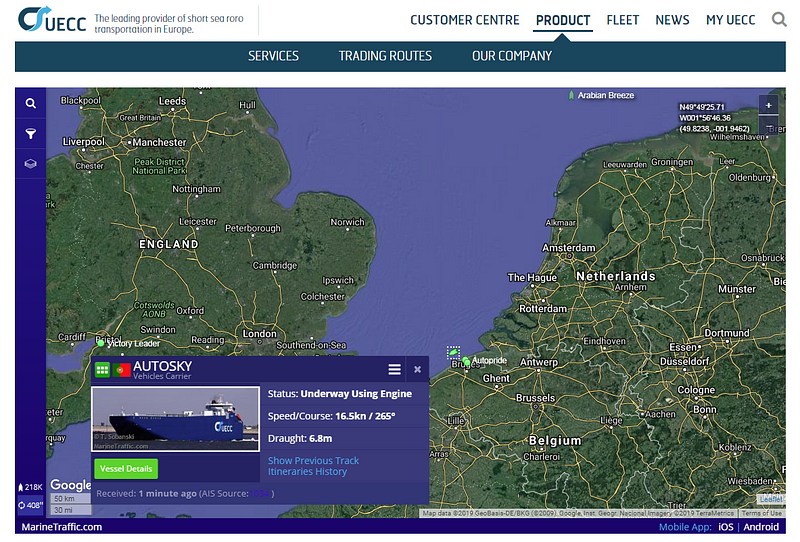
Using their website’s Product page I am able to see which ships in their fleet are currently en route. For this example, I selected the ship AUTOSKY and inspected it to find more details. If we click “Vessel Details” it conveniently takes us out to Marinetraffic.com.
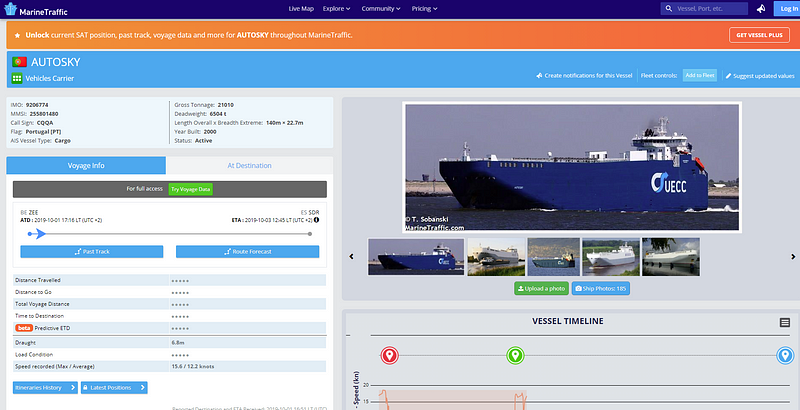
I tried searching for this ship in Maritime-connector but there were no jobs or crew listed so I moved to the next best thing... LinkedIn. I did end up finding some crew members listed here but more interestingly, I found a Financial Controller.
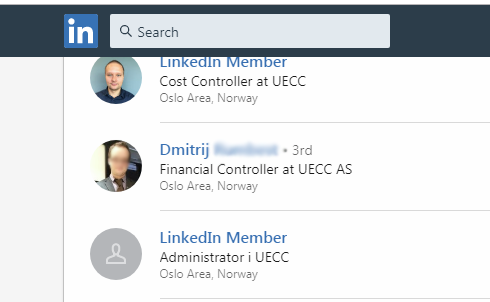
This Financial Controller does not keep his social media accounts very private. With a quick Google search, I was able to find his Facebook Page, website, and Instagram account. The details found here could be collected and used for potential phishing emails later.
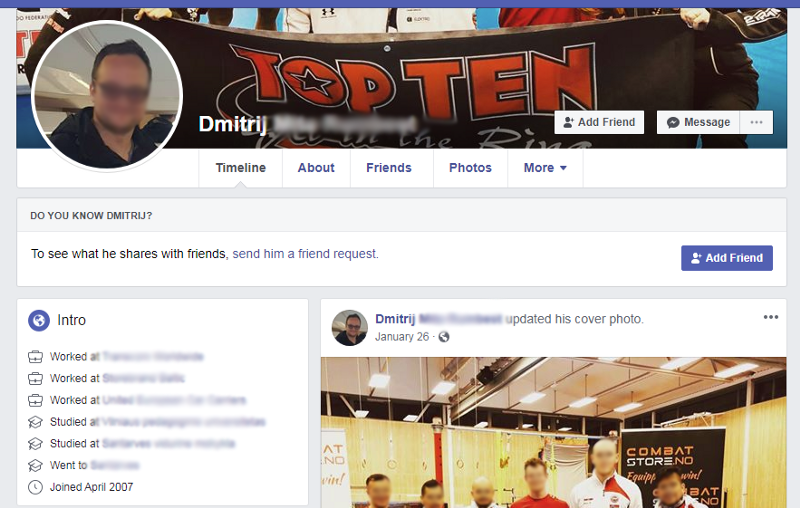
Now that I have gathered information on the shipping company and a specific ship in their fleet, a target individual in their financial department, along with the vulnerabilities in the Satcom system and Remote Desktop, I would be ready to move into a more offensive position and infiltrate their network. If offense was not my end goal, I would continue to work my way through the employee list to see if anyone leaks important details about their job online (badges, computer monitors, security systems, etc).
Using just a few websites we were able to find a plethora of useable info about these specific ships and crew members that could lead to an actionable offense plan. Please keep in mind these vulnerabilities are noted for educational purposes only!