Mitigating OSINT Threats within Schools and Universities

This week my university sent a message to be on high alert for a man who had been recently released from prison for threatening a professor with physical harm during a mental health crisis. The man had located the professor’s home and family and had threatened their safety. Physical safety concerns like this are happening all over the county and digital ransomware attacks on schools are becoming an everyday occurrence.
I considered how easy it would be to find actionable information on public schools and universities using OSINT techniques and how devastating the results could be. My goal with this blog is to spread awareness and shed some light on the ongoing problem with information leaks within the education system. We will take a look at the digital risks to faculty using the information found online and show how it translates to a physical safety risk. Then we will look at some documentation that provides concerning details about buildings and physical security and finally, what creepy things are available through Shodan.
Locating Faculty
Generally, we are all acutely aware of the threats to our children in schools but I am not sure faculty are always considered when security is put into place. It was scarily easy to track down specific information about members of faculty and trace them back to their homes, families, and frequently visited spots. For the purposes of this investigation, I chose one specific “target” to see how much danger they may be putting themselves in.
Organizational charts are readily available on most university or school sites and unfortunately, allow a person to determine a specific target name. Imagine a scenario where a student attended university but had to drop due to poor grades or a crisis and has been left with a huge amount of student debt. If this person felt scorned by the financial aid department they could use an org chart to determine a specific target.
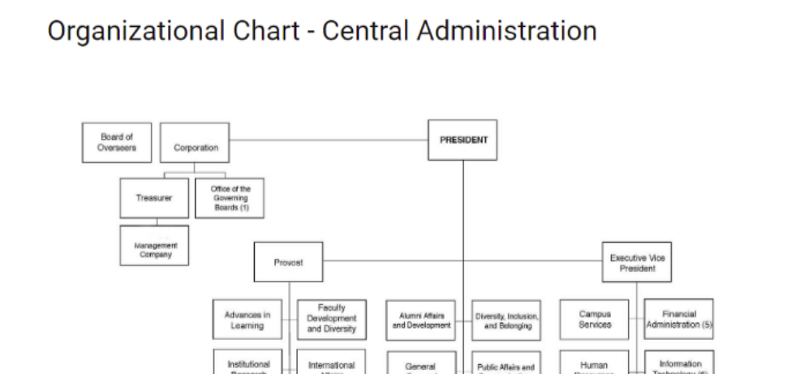
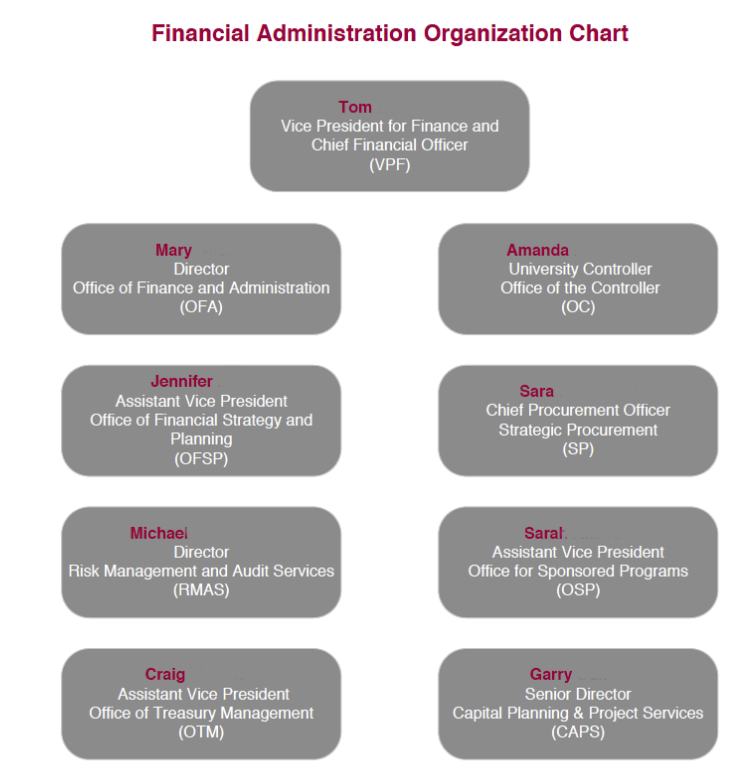
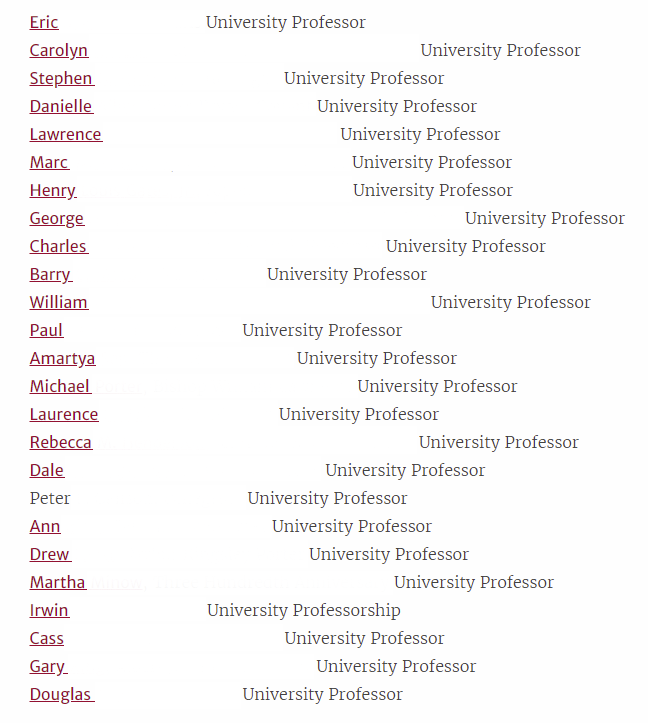
Some of the University sites even list the faculty in entirety. While I see the benefits of making faculty available, I also see the inherent dangers.
If we take a look at ratemyprofessor.com we often find detailed comments from students about professors and their backgrounds that are not posted elsewhere. Using this site, I chose a professor with a low rating to see what else I could determine about their identity.

This professor was very searchable on LinkedIn which provided me with past employers, connections, and job duties that may indicate where they will be located throughout their day.
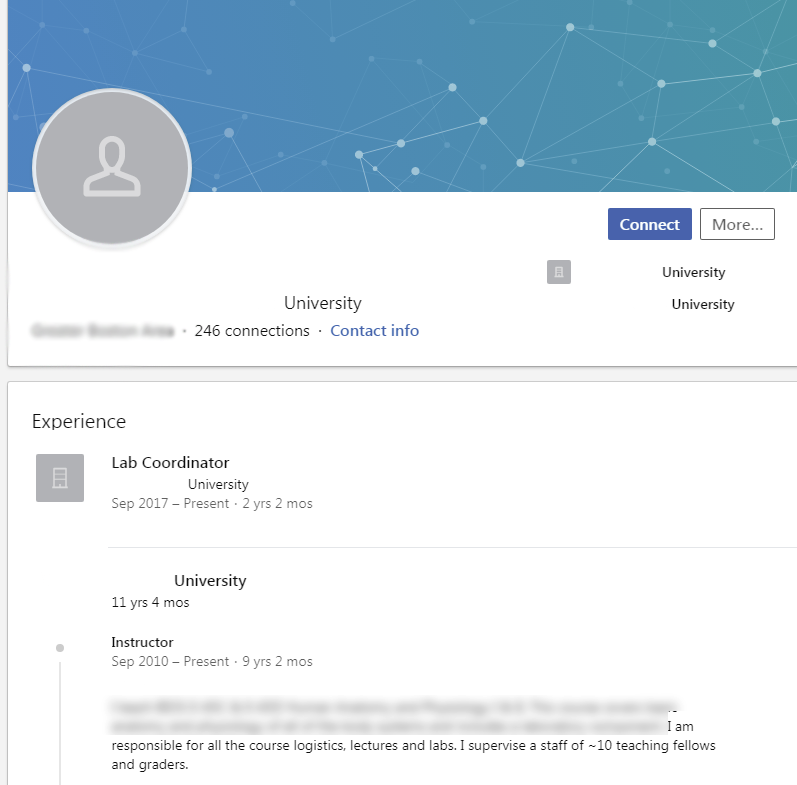
A Google search of their name led me to the University bio with a full name including middle initial and their gmail address.
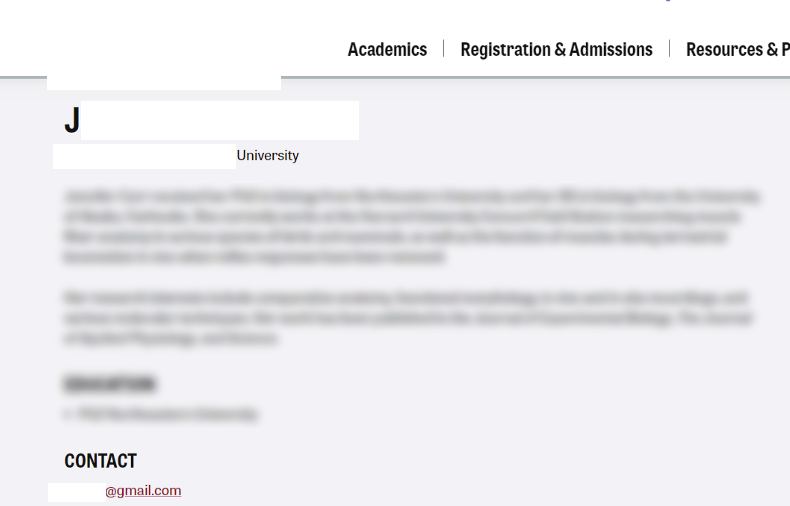
Using a people search site I was able to pull up an address and a list of known associates, one being their partner. Sometimes this information can be incorrect or old so I need to verify it.
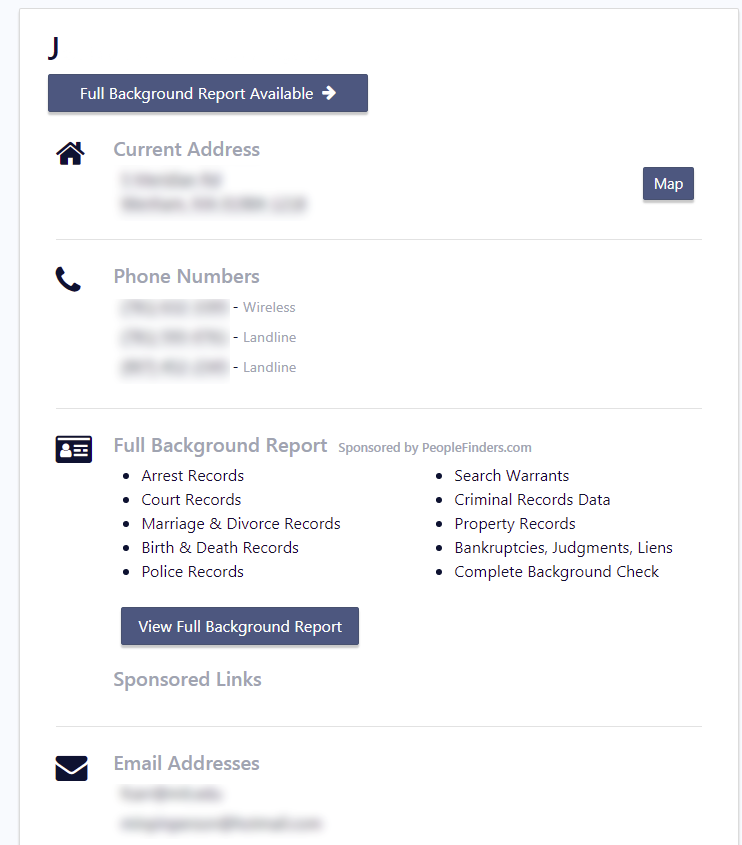
A Google search of the address listed in the people search gave me a picture of the front of the house. If I then combine the address+their name+their partner’s name I get a tax bill confirming their dual ownership of this specific property in 2019.

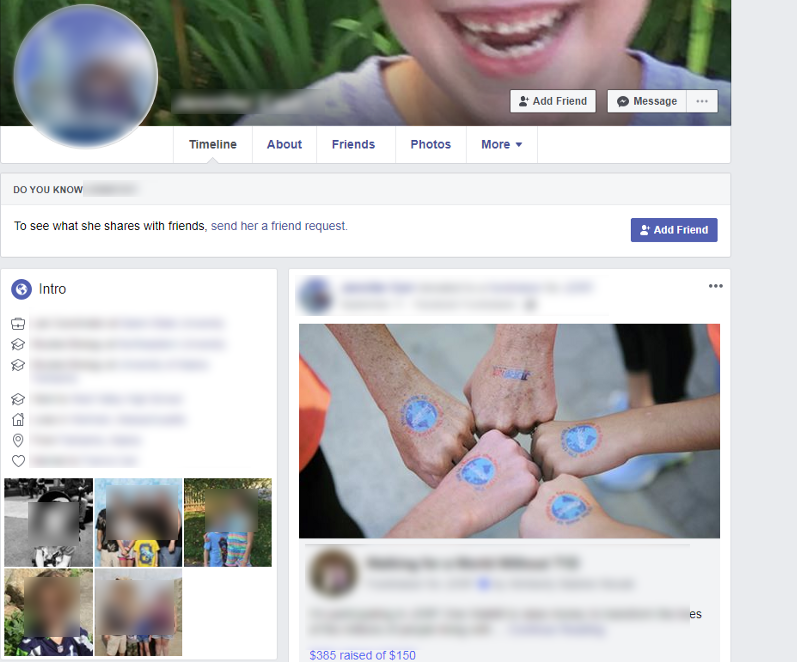
From this point, I decided to see what information existed on social media. At first, I assumed their profile would be locked down because being a teacher is dangerous these days. To my surprise, I found a wide-open Facebook page showing a complete About Me page, photos of the family, and photos of the inside of the house which further confirmed they actively live there. When I combine the information found on both the professor and their partner’s Facebook pages I have quite a dossier of information.
We can see by just this quick example how dangerous it is to leave all of your information open and available online, especially when working in a public job where we may make enemies we are not even aware of.
Building information
School systems, especially Universities, often provide detailed blueprints for their buildings online. Faculty use these maps to help plan events and students use these maps to help find classrooms. The risk I see when viewing these publically available maps is that an outside attacker gets access to the entire building blueprint showing entrances, exits, stairwells, etc.
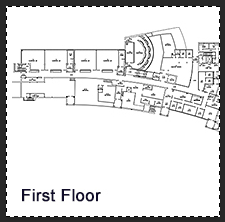
Location Information
Unfortunately, due to the routine nature of school schedules and activities, location information is pretty easy to come by.
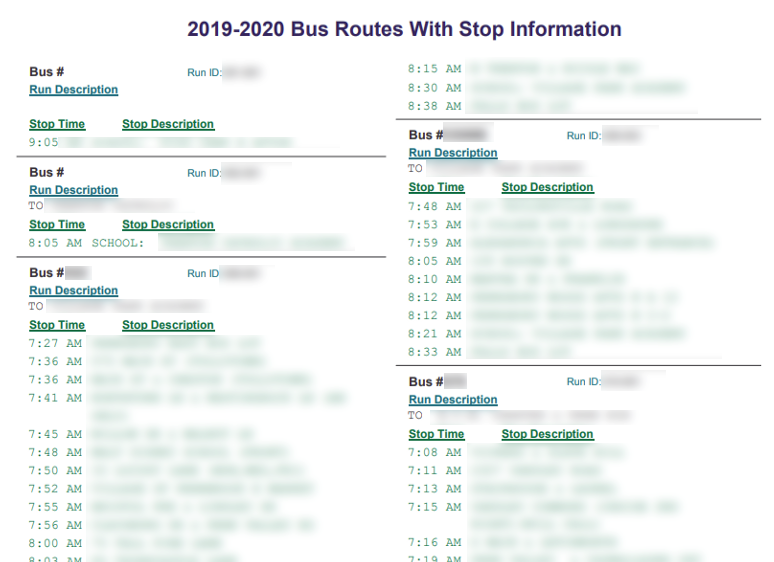
Many Elementary, Middle, and High Schools post their full bus routes with stop times so that parents know when to get their children to and from the bus stop. This is not intended to be alarmist, however, this gives predators very targeted times and locations to lurk around, especially if they are targeting a specific child.
Another area of risk might be the actual plans used to mitigate risk. Schools post pdf versions of their incident response plans for transparency as well as comfort for the staff, students, and parents. Without going into detail, a resourceful attacker might be able to use these plans to his advantage.

Open Webcams
When we talk about attackers in schools we often think about physical attackers with weapons storming the entrance. We also need to consider the unseen threat of someone hacking in and wreaking havoc on important systems on the network. Using Shodan, I was able to pull some interesting webcams from schools and Universities.
The below webcam seems fairly innocuous but if we watch it long enough we could pick up the patterns of the faculty and students throughout the day and possibly even security protocols.
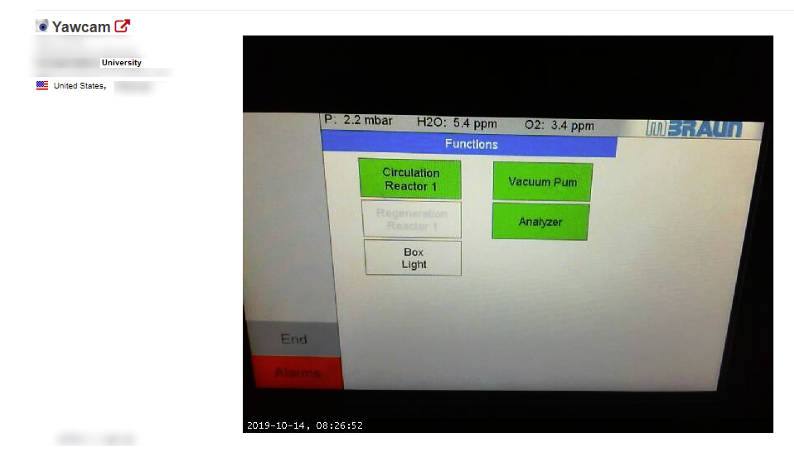
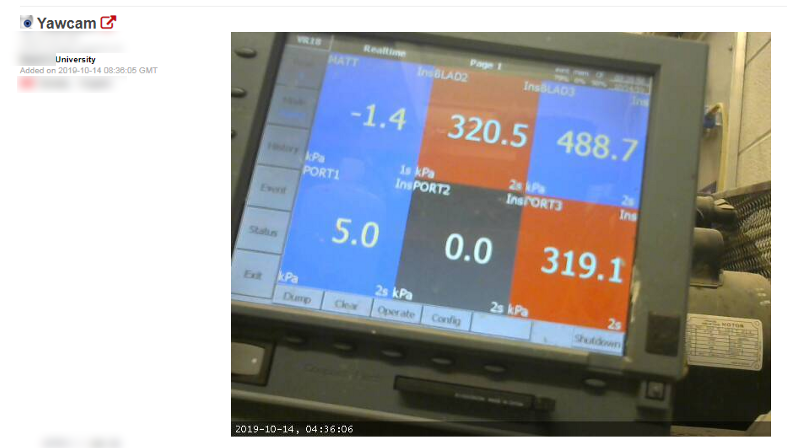
This webcam appears to be monitoring a gas line or cooling system. The concerning part about this is that the name of the system is clearly visible on the screen. This name allows a hacker to search vulnerabilities specific to this ICS as well as search Shodan for this device using coordinates.
Below is a similar situation where a temperature-controlled fridge is being monitored via open webcam. This cam has a few issues, first of which are the photos plastered all over the front. Second, as with the last cam, the name of the device is also on the front. If this fridge is connected to the internet it may be possible to find it via Shodan and use a vulnerability to shut it down. I am not sure what is stored within this fridge but I can estimate that it is probably valuable to the medical facility.

This is yet another example of a webcam monitored system, possibly pressure monitoring, openly available to the internet.
Remediation
Although all of this sounds very scary, there are some solutions we should consider for protecting school details and faculty/student privacy. Some of these remedies can have an immediate and tangible effect on security.
- All faculty should be trained and aware of basic security surrounding social media and sharing information in public.
- Schools and Universities should be cautious of posting emails with obvious name connections like “first.last@university.com” and instead use a mix of letters and numbers like “fnl5673@university.com.”
- Better care should be taken for many school documents and files that aren’t needed by the general public. These files should be kept behind authentication measures to limit access.
- Posting the names of students along with their location should be avoided (think soccer team player list +soccer game schedule). When possible, abbreviate names or limit it to “Name B.”
- Schools, daycares, and universities should immediately change the default username and password on their webcams to prevent unwanted access.
- If you have concerns, don’t be afraid to bring them up to school authorities! Sometimes an outside perspective on threats can cause them to reevaluate policies.
*This information is for educational purposes only.