The Hackable U.S. Prison System

When I think of the United States Correctional System I envision an underfunded prison filled to the brim with inmates. All of them packed into tiny cells with few luxuries aside from a chessboard with pieces carved from bars of soap.

OK, admittedly I have never been inside a prison and my only reference points are OZ and Wentworth on Netflix so maybe I am a bit out of touch with reality. I certainly never considered the colossal amount of technology necessary to keep a massive prison such as Angola safe and running smoothly. Once I began to look at the systems and processes, I was immediately concerned by how they might be exploited.
Humans
Social Engineering takes advantage of our natural inclination to trust and our need to help people and can be used to gain entry to buildings and systems. Security professionals are acutely aware of how easily people can be manipulated to give up data and even in high-security areas, humans can be the weak link.
In 2018, a man named Konrads Voits used social engineering and phishing to trick employees at the Washtenaw County prison in Michigan into installing malware to steal credentials. In a long-running campaign, Voits created a carbon copy of the Washtenaw County website ewashtenaw.org swapping out the w with v’s (ewashtenavv dot org). Voits then placed phone calls to employees pretending to be the IT department directing them to enter their credentials into the fake website to “update their computers” stealing over 1,600 county employee passwords.

Once Voits gained access with the stolen passwords his plan was to reduce his friend’s prison sentence. Luckily, he was detected before making the final adjustment to the prison records and he ultimately received a sentence of 87 months.
The success of Voits phishing campaign illustrates that despite being surrounded by steel doors and top of the line threat analysis software, prison employees who are poorly trained in digital security are a massive weak point in correctional institutions. A great way to mitigate this type of attack is through user education programs and self-testing internal phishing campaigns. Education helps to empower employees to ask questions rather than implicitly trust anyone who claims to be someone they are not.
Pay Phones and Commissary
Inmates now have the ability to make phone calls and visit with family or counsel via video. Encartele is a tech company that provides these services as well as some additional jail technology software such as content broadcasting. Devices like these should be placed behind a firewall for protection, however, many of these Encartele systems are open and available to the internet which allows us to pick them up on Shodan. From here it would be possible to find username/password and other telnet vulnerabilities. In the screenshot below, I did a search for “Encartele” in Shodan and picked up 17 in the U.S. alone.
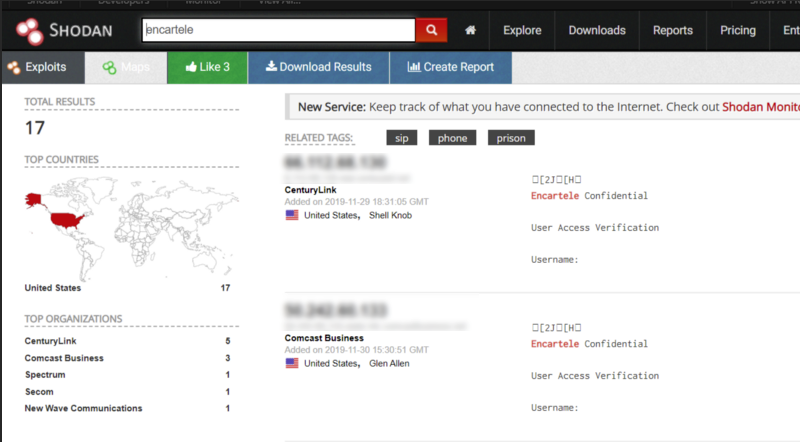
Similar third-party vendors to Encartele, like Securus Technologies, have had issues in the past with data leaks. In 2015, a data breach was reported at Securus that leaked 70 million voice recordings of prisoner phone calls with some alleged to be confidential attorney conversations. In 2018, prisoners in Idaho exploited Securus’s commissary Jpay system on their tablets and added $225,000 in credits to their commissary accounts.

Because the aforementioned prison uses tablets for JPay instead of PCs, the balance was likely stored on the machine rather than the JPay servers, making it accessible if someone were to hack into the SQL database.
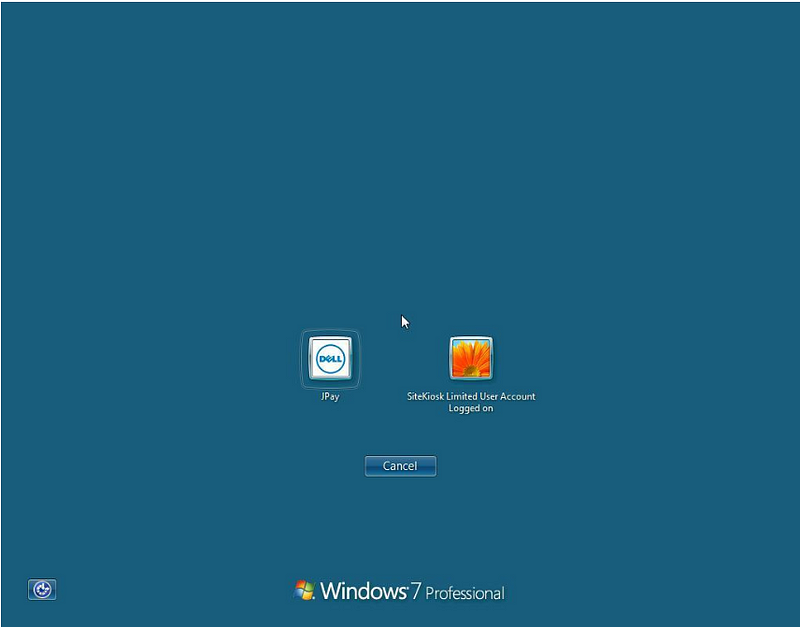
On Shodan, I was able to find several remote JPay logins including one on a Windows 7 system. If I were looking to get into the system I would start by checking whether this system was patched for the BlueKeep vulnerability.
BlueKeep (CVE-2019–0708) is a security vulnerability that was discovered in Microsoft’s Remote Desktop Protocol implementation, which allows for the possibility of remote code execution.
An increasing number of prisons are opting to avoid pay kiosks altogether and provide all inmates with tablets loaded with educational content, entertainment, and paid services that connect to their prisoner account. The tablets pictured below are similar to the tamper-proof tablets provided by a company called Global Tel*Link (GTL).

Their website states that GTL offers solutions for inmate communications, visitation (video), payments, investigations (intelligence as a service), facility management, and content.

Conveniently their website also lists which prisons use their technology and what services they have available at each location.
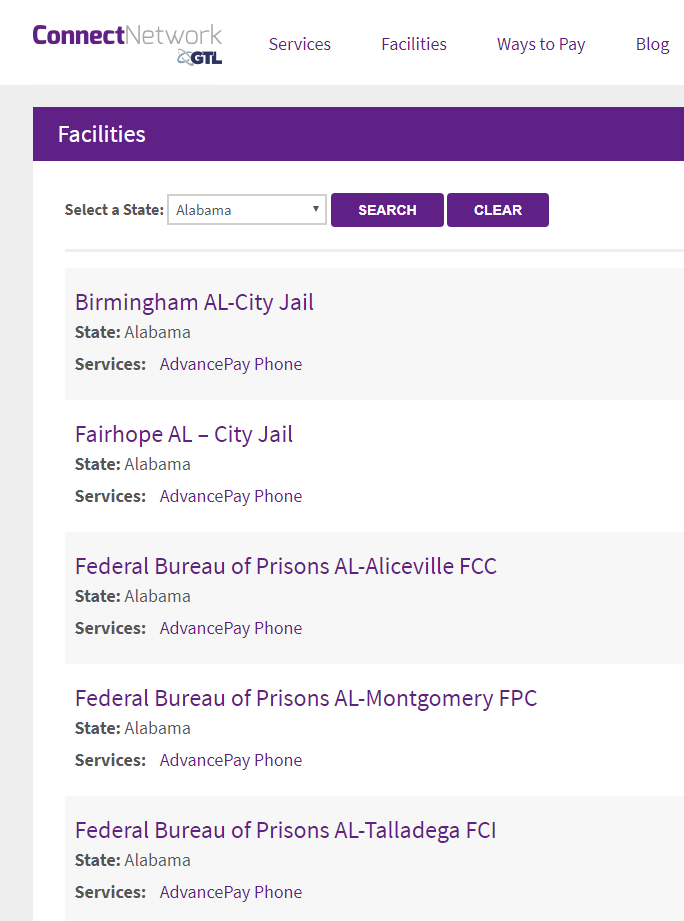
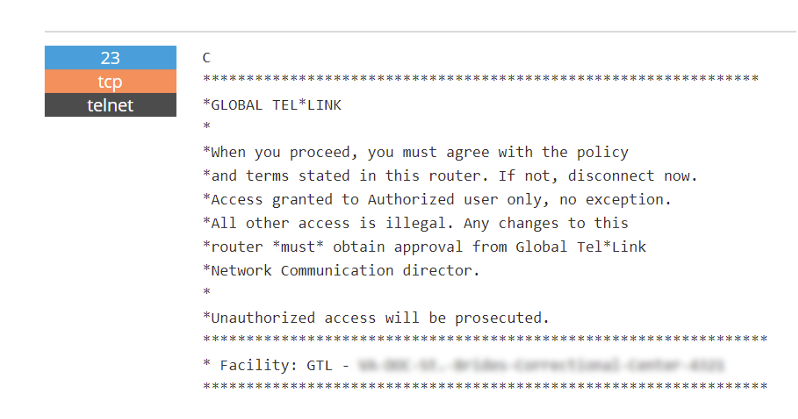
I hop onto Shodan and search for “Global Tel*Link.” I am able to quickly find a bunch of internet-facing GTL devices using Telnet that advertises right in the banner what prison they are located in. Telnet services can be dangerous because they are not encrypted so the data is passed openly between the telnet client and server causing logins and passwords to be captured easily.
Another possibility is that the default credentials may never have been changed and after running a scan on the router/device, an attacker could then telnet in using the default credentials.
Prison Control Systems
Prisons, as a rule, have hundreds of cell doors that need to be opened, closed, and locked electronically numerous times on a daily basis. For this, many prisons within the United States rely on SCADA (supervisory control and data acquisition) systems with PLCs (programmable logic controllers) to manage and make the system accessible remotely.
Because of the way the SCADA/PLC systems work and the numerous parts involved, they are often prone to an abundance of vulnerabilities. Since prison systems are not only comprised of door locks, but also things like video monitoring, shower controls, intercoms, and even perimeter patrol vehicles, if one part of this system is compromised it can make all of the other parts accessible to an attacker.

Once inside the system, there are numerous ways to exploit it. For instance, large prisons rely on a type of cascade system that opens doors in sections to avoid an overload of power to the system. An attacker could shut down the cascade system overloading the power and causing the doors to malfunction creating chaos and personal security risks.
In a 2018 research paper, Identifying SCADA Systems and Their Vulnerabilities on the Internet of Things: A Text Mining Approach, Sagar Samtani and his co-authors determined through Nessus scans that roughly 20% of SCADA devices from Rockwell Automation, Siemens, and Schneider Electric never had never updated/patched their software or changed the default credentials. According to my research into prison SCADA/PLC systems, the most commonly used brands are Allen-Bradley, GE Fanuc, Hitachi, Mitsubishi, Panasonic, Rockwell Automation, Samsung, Siemens, and Square-D. The odds of hitting a Rockwell Automation device that has default credentials is too high for comfort.
Prisons continue to increase their use of technology each year integrating things like Inmate Call Capture systems, AI to analyze and monitor threats, Drone Defense systems, Inmate Learning Management Systems, and even Teleheath options. With these technologies come inherent risks not only to personal information but actual physical safety.
Correctional institutions have a responsibility to make sure their systems are patched, up to date, and devices are not directly connected to the internet unless absolutely necessary. Because if I have learned anything from watching old episodes of Locked Up, it is that inmates are nothing if not resourceful.

All screenshots are for educational purposes only, please do not hack a prison unless you want to be inside one. Special thanks to @lokinLaufey and zer0uid from PA Hackers for helping me make sense of some data.