Maritime OSINT: Port Analysis

Why is port analysis important to us as OSINT Analysts? There is an increasing need for the overall surveillance and analysis of maritime ports due to the increase in global trade, smuggling of goods/people, COVID tracing and medicine transport, terrorism, and shipbuilding/breaking. The intention of this writeup is not to wax poetic about maritime tools, but rather to inspire some outside the box thinking and methodologies that may assist in your investigations.
Before we dive in, let’s define what a port is and what happens there. A port is a location where vessels can load/unload various cargo and people. Special amenities are generally offered such as warehouses, fishing facilities, infrastructure equipment, workshops, as well as restrooms and medical facilities. Ports are home to the Port Authority which manages all maritime services, activities, navigational safety, and security within the country’s waters. There are several types of ports: inland ports, fishing ports, dry ports, warm water ports, and seaports the most common due to commercial shipping.

Ports are often the entry and exit point for nefarious activities, such as the trafficking drugs, weapons, and humans. As an analyst you might be tasked with tracing smugglers from the Law Enforcement/Customs side, developing attack profiles for the ports themselves, or even working on an investigative journalism piece that requires maritime knowledge. Whatever the case may be, there are numerous data points to research when scrutinizing shipping ports.
I am well aware that Customs has access to all sorts of fun tools that we don’t have. Things like thermal CCTV cameras, drones, artificial intelligence, and even new tech that can detect pyruvic and lactic acid emitted by humans in small spaces. Don’t let that get you down; I will show you that there is still quite a lot we can track through open-source intelligence alone.
Begin by asking yourself some key questions:
- What is the scope of this investigation?
- Who is coming and going from the port?
- What cargo are the vessels carrying?
- Does anything stand out on historical satellite imagery?
- Are there any anomalous patterns in traffic?
- Does anyone work at the port that could be compromised?
- Does this port have a history of nefarious activity?
For this writeup I chose to use 2 of the busiest ports in the US as my example. The ports of Los Angeles and Long Beach serve as an international trade gateway between the United States, China, Japan, and South Korea. Analyzing these ports on the west coast, we will gather some open source intel for each.
As a rule of thumb, when I am investigating a location I have never been to I will pop open Google Earth or IntelliEarth and check it out. We can see from the images below just how close satellite imagery can zoom in these days. Often, words on buildings, streets, and in this case ships are completely legible. We can also view changes to the port itself such as construction or the movement and storage of particular cargo through historical satellite images. Skip backward or forward a few years in time and see what changed and where things have moved.
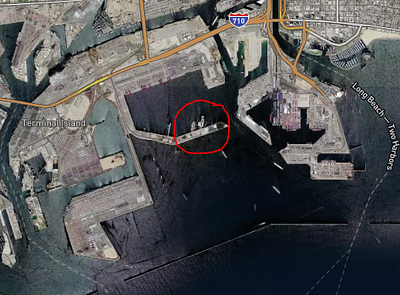


It is apparent that the main function of a port is the entering and exiting of marine vessels, therefore tracking them becomes integral. There are a multitude of sites that are able to track ship paths, but they tend to be partially hidden behind a paywall. The free data, however, still proves to be very useful for enumerating new pivot points.
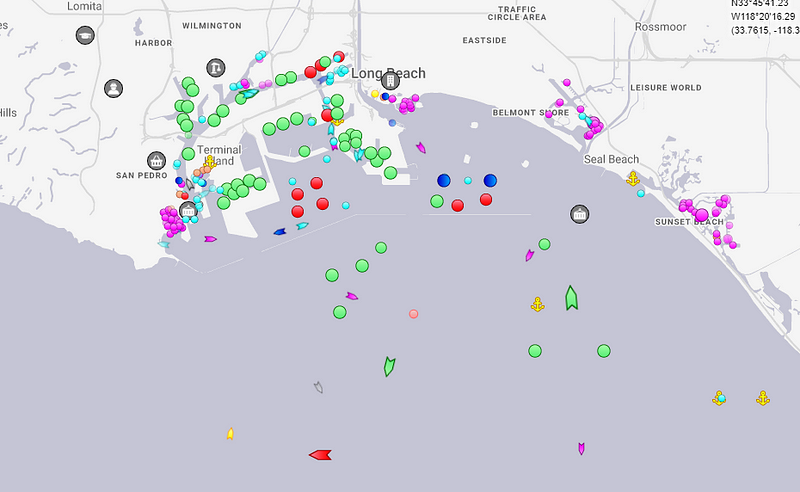
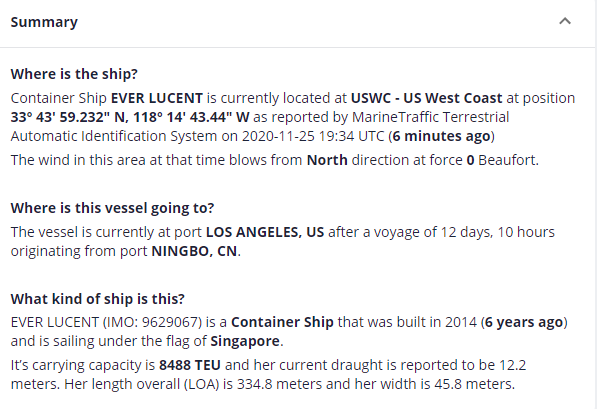
The screenshots below were taken from MarineTraffic.com which, like all of these sites, uses the Automatic Identification System (AIS) to track the real-time position and information about small and large vessels. AIS data is handy for determining things like which country a ship departed from, their time of departure/arrival, the flag the ship sails under, what the name and type of ship it is, and so on. I chose to randomly investigate the container ship Ever Lucent which, at the time of writing this is chillin’ in the Port of os Angeles, having departed from Ningbo, China.
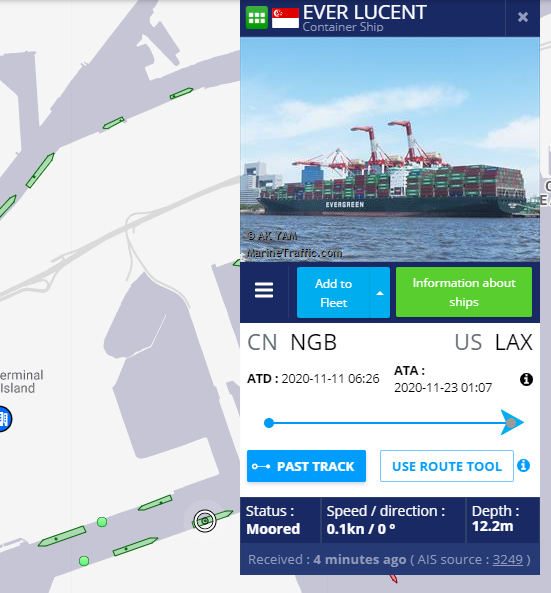
Looking deeper, we can see that the Ever Lucent is carrying Hazard D cargo under the flag of Singapore, and the ship call sign and numbers are available.
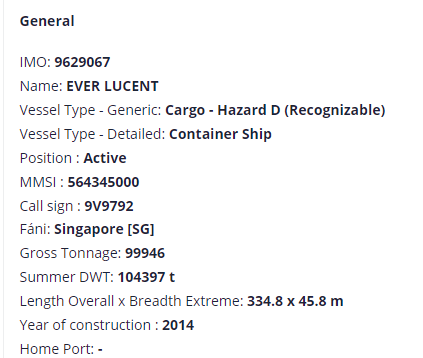
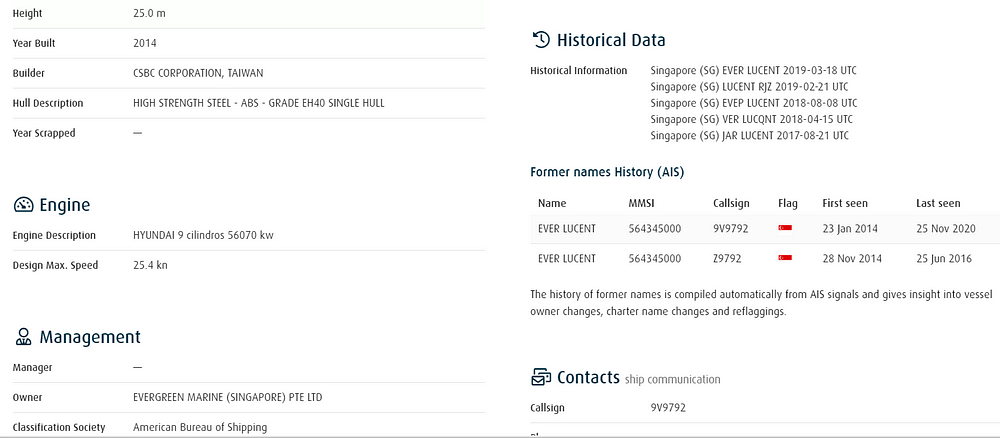
I never like to rely on just one source when digging into a target, so I also ran a search for Ever Lucent on Fleetmon, which did turn up a few additional details. Fleetmon shows the builder name as CSDC Corporation, Taiwan and the owner as Evergreen Marine (Singapore) PTE LTD.
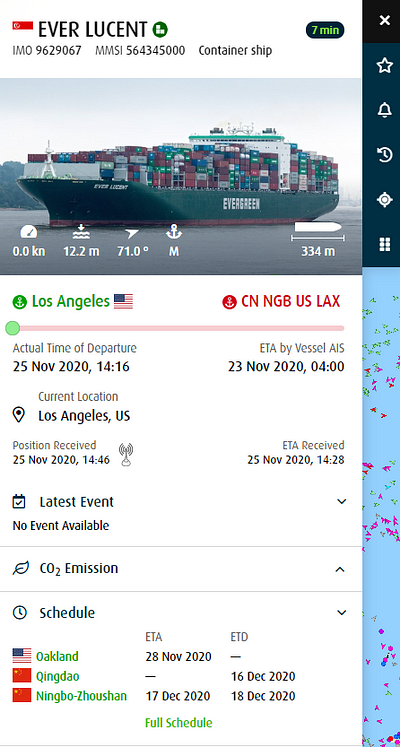
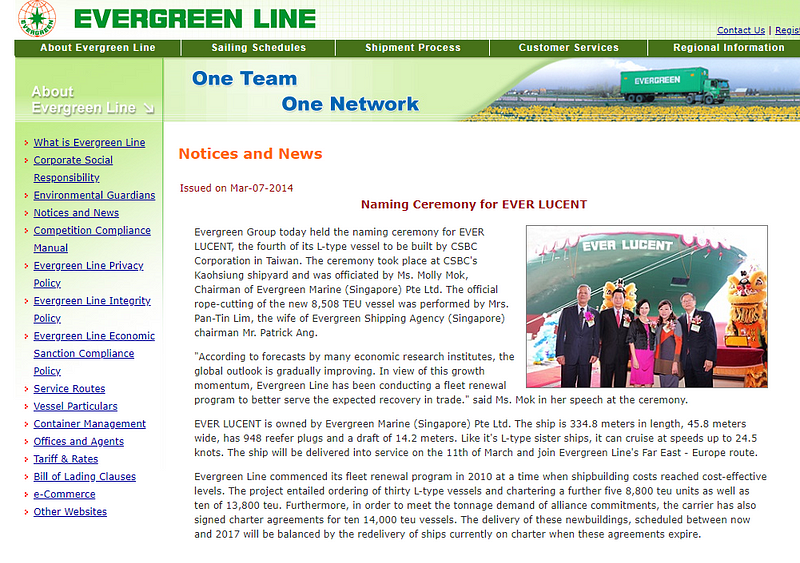
Already we have gathered quite a few data points for further investigation! From here a good plan of action is to pivot to contract sites like GovTribe or GovWin and look into the contracts Evergreen holds. Contracts lead to where money is being spent, which generally leads to more intel. I also like to Google Dork for documents or articles relating to my subject. Often companies will disclose useful information on their website About Us pages or in company bulletins. An example of this is the webpage below that I found by searching “Evergreen” and “Ever Lucent.” This page tells me that the Ever Lucent was built by CSBC, and that Mrs. Pan-Tin Lim is the wife of the shipping agency chairman Mr. Patrick Ang, among other details. Don’t discount the power of a simple Google search!
Now that we have tracked the ship down and learned who owns it, who built it, where it is coming from/going, we should consider what the ship is delivering. Unfortunately, tracking down the actual cargo proves to be difficult without specific cargo numbers. Sometimes we can look to social media or ship enthusiasts to unknowingly leak information.
Ship tracking sites often feature photos taken by ship enthusiasts admiring the voyage of a large sea vessel. I was able to locate a photo of Ever Lucent taken soon after loading up its cargo. I was unsuccessful at making out the numbers on these containers, but it may be a plausible option in some cases.

If you are lucky enough to locate a container number, it can be searched on the site Fleetmon. Another cool feature that Fleetmon offers is a Port Database that displays specific details for the port including weather, usage, and vessels currently in port.
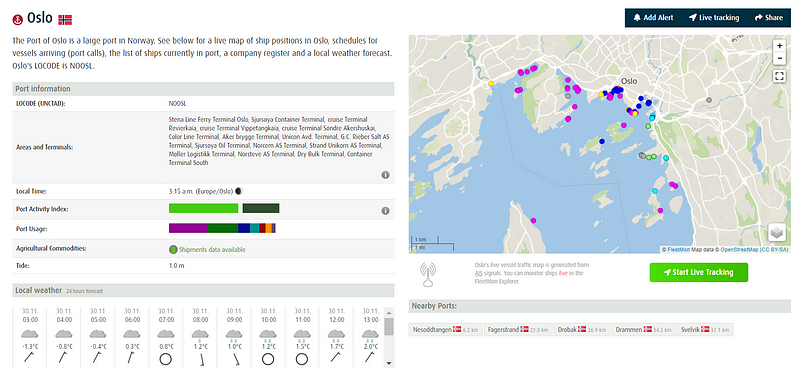
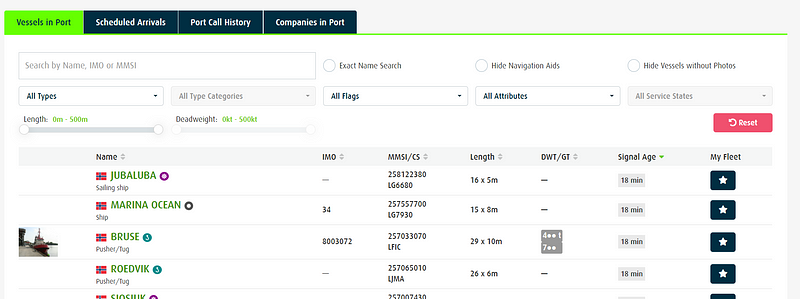
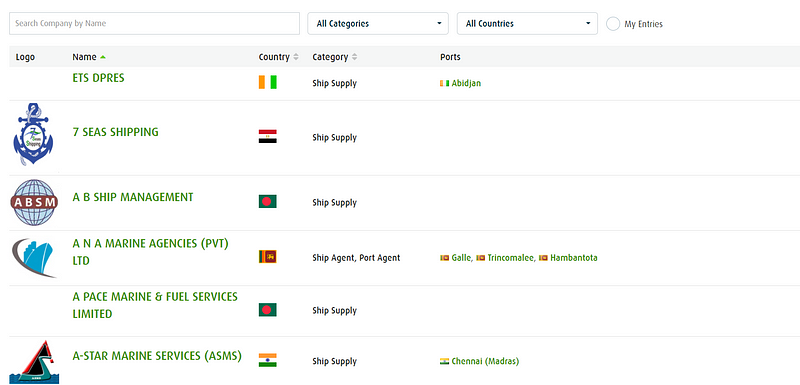
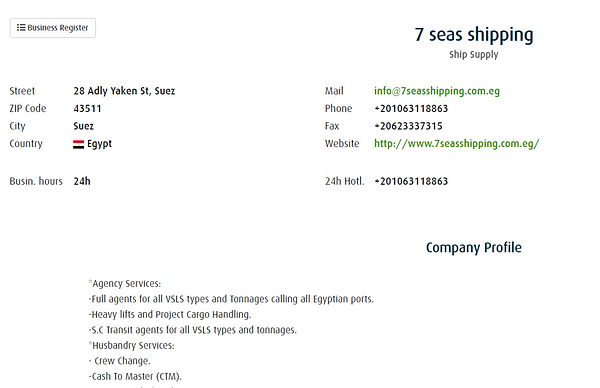
Again, some items are hidden behind a paywall, but the Maritime Business Register is not. We can search the register by country or name to find businesses related to shipping, agencies, inspection, dining, etc. The profiles show contact information and additional details that can be used to pivot.
Alas, I could write endlessly about ports and ships, but this is growing long. The final item I want to discuss here is not the port itself but rather the shipping crews, port workers, and passengers that flow through the port and terminals each day.
As shipping expands, smugglers benefit from the increasing size of overloaded container ships (some autonomous) as they hitch a ride from port to port with shipments of cocaine, heroin, and other drugs. In particular, the Group America gang has smuggled more than 5 metric tons of cocaine over the past 20 years by acting as a middleman between producers and wholesalers.

In 2009, the gang was caught smuggling 15,582 bricks of cocaine by using the ship’s crane to bring the sacks on board from smaller vessels. Several crew members were involved in placing them within resealed boxes inside seven shipping containers.
From this story alone, it is easy to see why analyzing a ship’s crew as well as port personnel is vital. Port employees also risk exploitation through blackmail and spear phishing, which may pose a threat to critical infrastructure.
With a Google Dork we can easily locate a current Port of Los Angeles employee. From a cyber security standpoint, I want to search for someone who has a potential high level of access to the port systems.
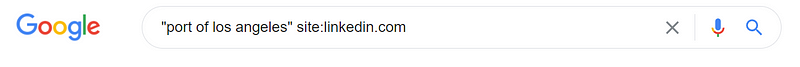
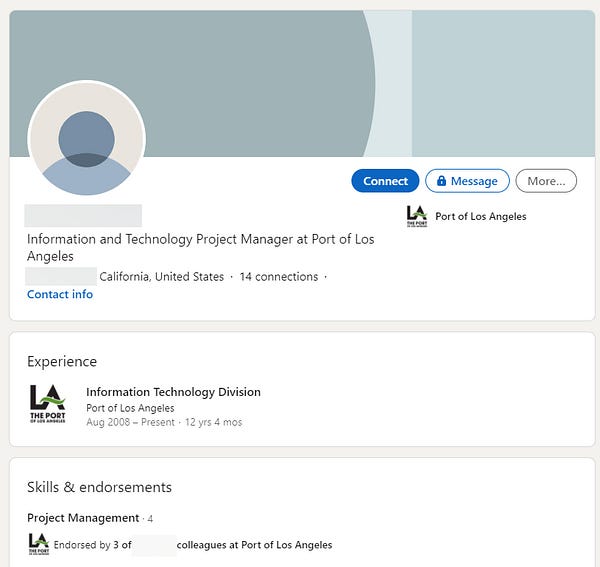
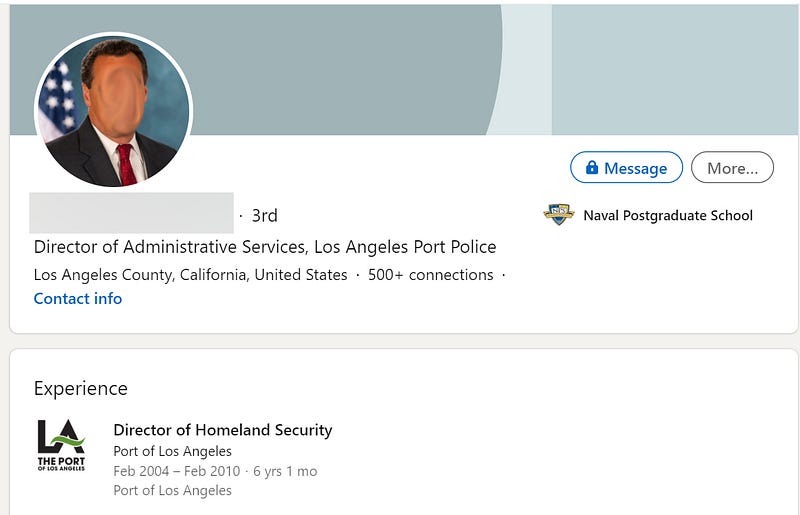
A few pages in, I find both an IT Project Manager and Director of Homeland Security for Port of Los Angeles. At this point, I would try to enumerate emails for these individuals, as well as any additional targets.
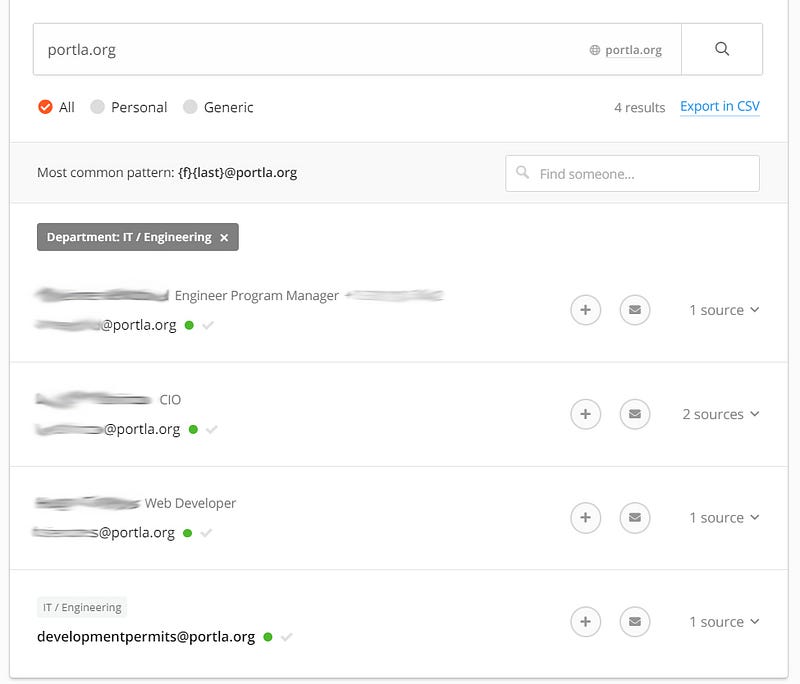
Jumping over to the portoflosangeles.org website, all the way at the bottom in the footer we get an email address. Using this email I can drop the domain into hunter.io and see what other emails pop up.
Eighty-eight emails are found for portofla.org, but four are listed as being specific to IT/Engineering. One of these names happens to be a Chief Information Officer.
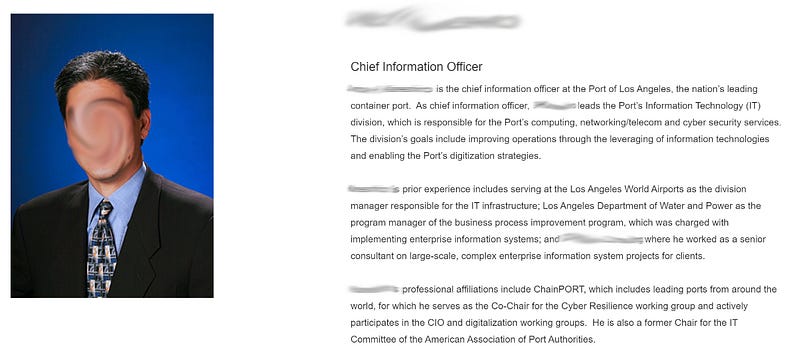
Googling this person brings up their career biography with many useful details like how their department is responsible for the Port’s computing, networking/telecom, and cyber security services.
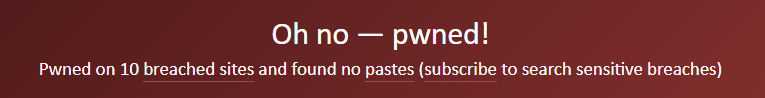
We can then drop their work email into haveibeenpwned to check for possible breaches. In this case, our person has been in ten breaches and several of these breaches contain plain text passwords. Unfortunately, it is just that easy for someone to be compromised and with a potentially catastrophic effect reminiscent of the Maersk attack in 2017.
An increasing number of vessels are being designed to run autonomously, from cargo ships to Navy warships. Threats to port infrastructure are a very real possibility, these including things like ransomware attacks, rerouting of ships, capsizing, sabotage, tracking specific cargo to seize, and collisions. Entrance to the systems could be gained through breached credentials/credential stuffing.
When we think of critical infrastructure security, ports are not often the sexiest area to focus on. However, they are a critical point of contact for smugglers, terrorists, theft, and sabotage to our supply chain that must be taken seriously. My hope is that I have provided a few useful tools and ideas to help you investigate. If anyone has any additional tools or methodologies related to port OSINT I would love to hear about it!